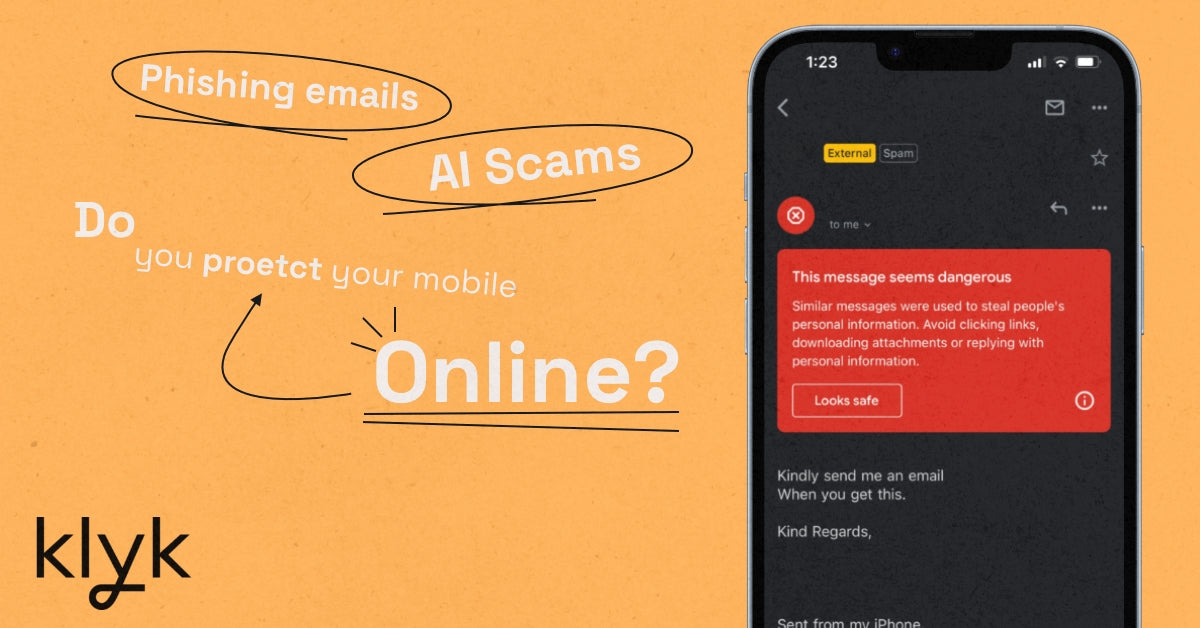
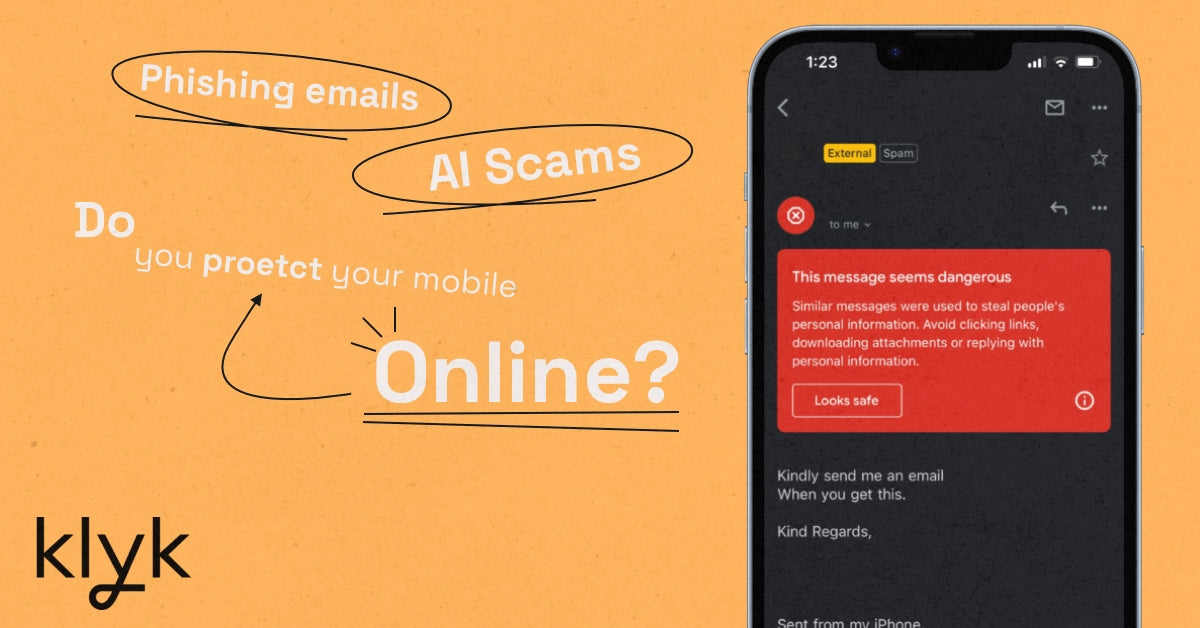
In today's digital age, mobile devices have become essential to our daily lives. From banking, personal use, and work data, we rely on them for almost everything. However, this dependence also makes us vulnerable to various security threats that can compromise our professional and personal information and privacy. This blog discusses security measures you need to take to protect yourself and your mobile devices when online and in the real world.
7 steps to protect yourself and your mobile devices whenever you're online
Keep your device up to date
One of the easiest ways to ensure your device's security is by keeping its software up-to-date. Manufacturers regularly release updates to fix security vulnerabilities and improve performance. You can switch on automatic updates to ensure your device always has the latest software and security patches.
Use a strong, unique password
Your device's password is the first line of defence against unauthorised access. Use a strong, unique password with a mix of upper and lowercase letters, numbers, and special characters. Avoid using easily guessable passwords like "123456" or "password." Additionally, don't reuse passwords across different accounts and devices. Always lock your device when not in use to prevent unauthorised access. Use biometric security features like fingerprint or facial recognition, if available, for added security.
Install a reliable antivirus app
A good antivirus app can help protect your device from malware, viruses, and other threats. Choose a reputable antivirus app from a trusted source and keep it updated to ensure maximum protection.
Be careful with app permissions
When installing apps, pay attention to the permissions they request. Only grant permissions that are necessary for the app to function and be cautious of apps that ask for excessive permissions. You can manage permissions on almost all Android and iOS device settings. Additionally, only download apps from trusted sources, such as the official app store for your device.
AI Voice Dubs
Another emerging threat is the use of AI-generated dubbed voices pretending to be family or friends. These voice impersonations can sound uncannily similar to your loved ones, making it difficult to discern whether the person on the other end of the line is genuine. For example, if you get a call from someone claiming to be your sibling and asking for sensitive information or financial help, you can ask them to provide the safe word. If the caller doesn't know the safe word or refuses to share it, you can conclude that the call might be a scam and take appropriate action.
Be aware of phishing scams
Phishing scams use deceptive emails, texts, and websites to trick users into providing sensitive information or downloading malware. Be cautious of unsolicited messages and verify the sender's identity before clicking links or downloading attachments. For example, you might receive an email from what looks like a manager or CEO asking for a paid task to be completed. Without taking extra precautions, you and whoever else received that email could become part of a scam which could hurt the company.
Be cautious of your surroundings when dealing with sensitive data
When showing sensitive data on your mobile device in public, you must be aware of your surroundings and take precautions such as using privacy screen protectors & password managers. Password managers are secure, encrypted storage solutions that enable users to store complex passwords and other sensitive data without having to remember them. This eliminates the risk of typing your password in public where it could be seen by potential malicious actors.
Stay vigilant and proactive in protecting your personal and work devices, and enjoy the convenience of technology without compromising your security and privacy.
Work with a trusted partner
While there are numerous steps individuals can take to protect themselves and their devices, the landscape of cybersecurity is constantly evolving, and staying ahead of threats is a demanding task. That's where Klyk steps in. As your trusted partner for IT strategy and security, Klyk provides robust protection for your business. We stay on top of the latest trends and threats, offering advice and solutions that are tailor-made to your specific needs. We ensure that your business is not just reactive, but proactive in its approach to cybersecurity.